Operating Systems
- Windows XP (32 and 64 bit)
Vulnerable Products
Test Procedure
- On a Windows XP computer, open Windows Explorer (e.g., by double-clicking "My Computer").
- Copy the following location to Windows Explorer's Address field, press Enter and wait up to 30 seconds. Try the 32-bit location first, and only if the test fails and you're using 64-bit Windows XP, also try the 64-bit location.
32-bit location: \\www.binaryplanting.com\demo\program_manager_group_converter
64-bit location: \\www.binaryplanting.com\demo\program_manager_group_converter_64
- At this point, one of the following is likely to happen:
- Windows Explorer displays the content of the remote folder as shown below.
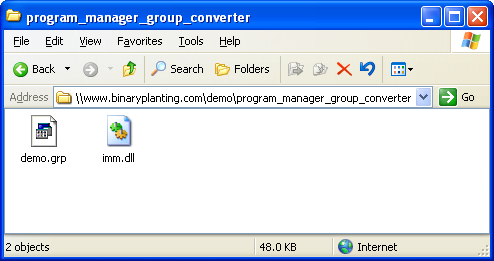
- Or, some error message pops up describing that the remote folder could not be found or displayed.
- Or, nothing happens.
- In case Windows Explorer hasn't shown the content of the remote folder, and you either got an error message or no response at all, first try again a few times, then try with a freshly opened Windows Explorer, then log off and log on again, and finally restart your computer and retry. If all these attempts fail to display the content of the remote folder, the test is over and you can skip to the results
- If, however, Windows Explorer has displayed the content of the remote folder, double-click on file demo.grp. If this results in a "HACKED" dialog popping up like the one shown below, you are currently exposed to binary planting attacks originating from the Internet (see the results).
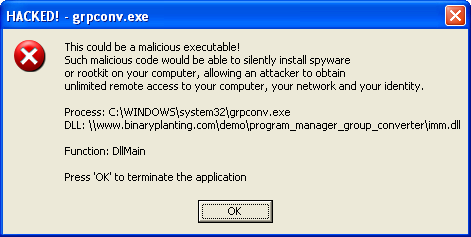
If, on the other hand, double-clicking on the file doesn't launch a "HACKED" dialog, retry a couple of times. If this fails to produce a "HACKED" dialog, the test is over and you can continue to the results.
Test Results
As a result of the above test, one of the following has happened. Find your own result in the table below and read the diagnosis of your exposure.
| Your result |
Diagnosis |
| Your Windows Explorer hasn't displayed the content of the remote shared folder. |
If all your attempts to see the content of our shared folder failed, the reason is likely one or more of the following:
- WebDAV communication between your computer and our server is being blocked either by your network or personal firewall. If this is the case, you are probably not exposed to binary planting attacks originating from the Internet. Note that you may still be exposed to binary planting attacks originating from your local network, and even from the Internet if you connect your computer to another network, such as to a wireless network on a business trip.
- Your Web Client service is not running. (This service is running by default on Windows Workstations, but not on Windows servers.) If this is the case, you are probably not exposed to binary planting attacks originating from the Internet. Note that you may still be exposed to binary planting attacks originating from your local network, and even from the Internet if you connect your computer to another network, such as to a wireless network on a business trip.
- Your Windows system is not up-to-date. For instance, Vista used to have functional problems with accessing certain WebDAV shares and our shares seem to be of such type. Make sure to update your system with the latest updates, then redo the test.
|
| Your Windows Explorer has displayed the content of the remote shared folder, but double-clicking on the file hasn't launched the "HACKED" dialog box. |
If opening the file from our server failed to launch the "HACKED" dialog, the reason is likely one of the following:
- The provided file's extension (.grp) is associated with some other application than Microsoft Program Manager Group Converter. In this case, your exposure to binary planting attacks is unknown, as the test failed to address the vulnerable application. While the particluar vulnerability used for this test seems to be "unreachable" for a remote attacker, nothing can be determined about your general exposure to binary planting attacks. You can do two things: (1) try some other tests that we provide, or (2) retry the same test on another computer in your network which possibly has the original applications associated with our data files.
- The targeted vulnerability may have been fixed by the vendor. In this case, your exposure to binary planting attacks is unknown, although one of the many vulnerabilities has apparently been eliminated. You can try try some other tests that we provide.
- Your network or personal firewall, while allowing browsing remote WebDAV shares, blocks the downloading of potentially dangerous binaries. If this is the case, you are probably not exposed to binary planting attacks originating from the Internet. Note that you may still be exposed to binary planting attacks originating from your local network, and even from the Internet if you connect your computer to another network, such as to a wireless network on a business trip.
- You have Microsoft's CWDIllegalInDllSearch hotfix installed and configured so as not to allow loading DLLs from remote WebDAV shares. If this is the case, you are probably not exposed to binary planting attacks originating from the Internet or from local shared folders.
|
| Your Windows Explorer has displayed the content of the remote shared folder, and double-clicking on the file has launched the "HACKED" dialog box at least once. |
You are currently exposed to binary planting attacks originating from the Internet through at least one existing vulnerability. A remote attacker can exploit either the vulnerability in Program Manager Group Converter used in this test, or any other similar vulnerability that may exist in applications installed on your computer. Furthermore, other computers in your network are also likely to be exposed as there seems to be no network-wide countermeasure in place.
|
For additional information, go to ACROS Security and ACROS Security Blog.
Please kindly direct any feedback regarding this test to security@acrossecurity.com.
|